Zabbix server setup
The Zabbix server must be affiliated with a specific company and accompanied by a root user. This root user is essential for carrying out administrative tasks, such as creating service users and Zabbix user groups on the associated Zabbix server.
Zabbix server list
The Zabbix server page of DataForge contains a list of all integrated Zabbix servers:
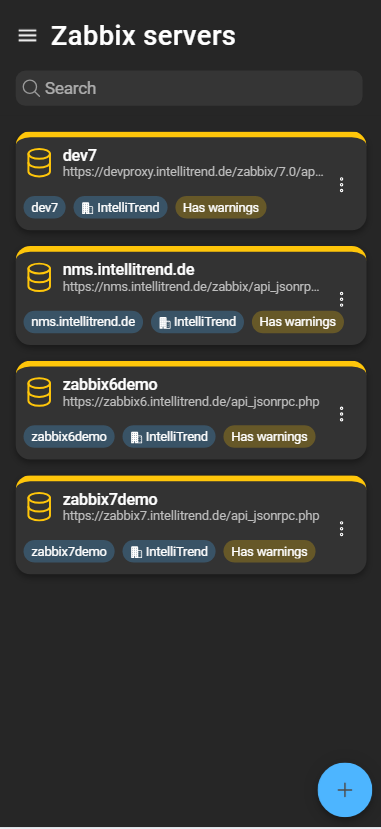
Each added server is represented by a card and feaures additional information about the server. This includes:
- the server’s name
- the server’s identifier
- the company the server was added to
- information about synchronization warnings
- a context menu
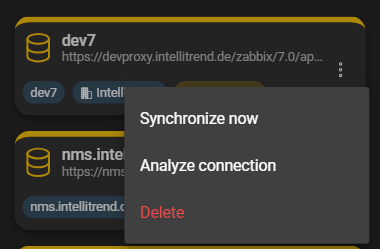
- Synchronize now: Manually start the synchronization process. Usually not necessary as DataForge synchronizes regularly by itself.
- Analyze connection: Further explained later in this chapter.
- Delete: Removes the server from DataForge.
Add a Zabbix server to DataForge
To integrate a Zabbix server, you need the necessary permissions to add Zabbix servers.
Navigate to the Administration > Zabbix servers page and click the blue plus. This will open the general section of the wizard:
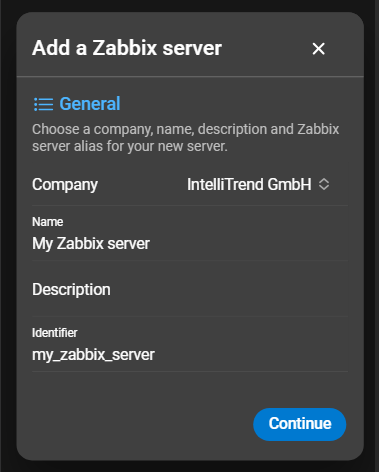
- Company: Select the company to which the server will be associated.
- Name: Choose a name for the Zabbix server.
- Description: A description for the added server.
- Identifier: This serves as the
Zabbix server identifierwhile adding a DataForge user account.
To continue click the corresponding button, this will open the Connection section:
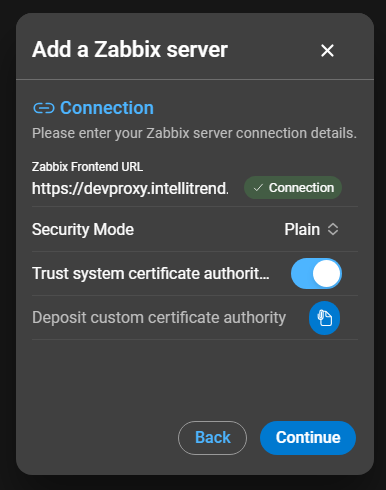
- Zabbix Frontend URL: Enter the complete
URLrequired to access the Zabbix frontend API endpoint. - Security Mode: Choose between
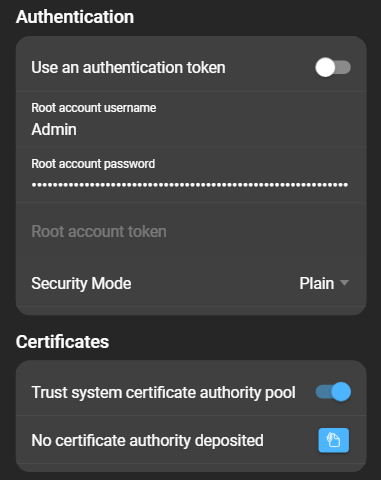
Plain,Basic Auth, andAPI Guard*. - Trust system certificate authority pool: Switch to toggle to trust the system certificate authority pool.
- Deposit certificate authority: If system certificate authority pool is not trusted, upload the CA-certificate in this field.
IntelliMon API Guard:
The API Guard is a free software from IntelliTrend that offers an extra layer of security. It acts as an API reverse-proxy/gateway for a Zabbix frontend, allowing public access to the Zabbix API without exposing the entire web frontend.
If you want to learn more about the IntelliMon API Guard or get it for yourself, check out the following pages:
Click continue to proceed to the Authentication section:
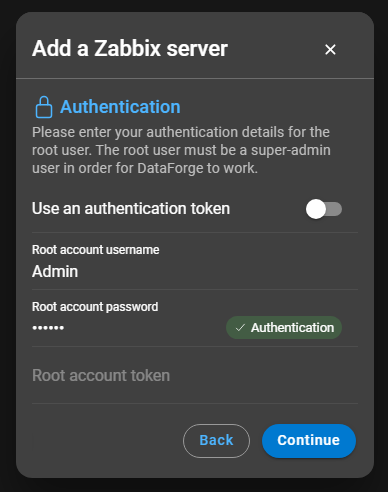
- Use a authentication token: Toggle this option if you want to use an authentication token instead of a username and password.
- Root account username / password: Provide the Zabbix root user’s credentials in these fields.
- Root account token: If you opt for token-based authentication, enter the Zabbix user token here.
Proceed to the S3 object storage settings by continuing:
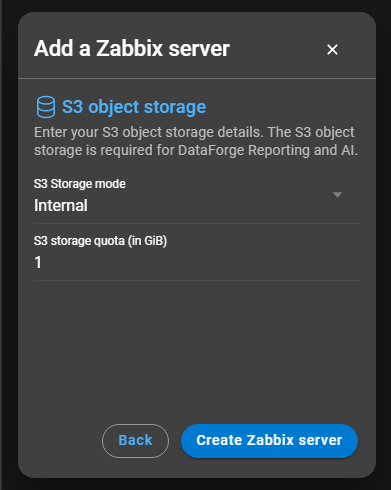
By clicking Create Zabbix server the process will be finished and the server appears in the server list.
Zabbix server configuration
You can update your Zabbix Server by clicking the configuration icon of the server you want to inspect or update. The configuration is split in four sections:
1. Warnings and General
The general section consists of the configuration that was specified when the server was added. It is not possible to edit the company.
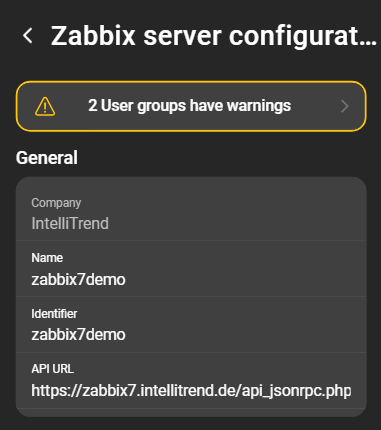
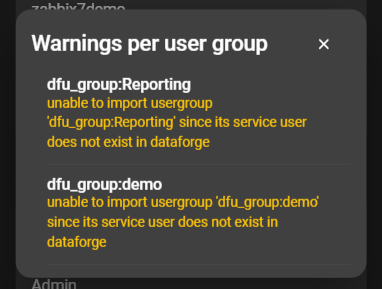
Warnings regarding the Zabbix user groups are displayed first in the Zabbix server configuration. When the box is clicked, a modal opens with an overview of all warnings:
2. S3 Object Storage
The S3 object storage is used to store generated reports, AI datasets, models and tests.
There are three Storage Modes you can choose between:
Internal
Internal will use the instance provided S3 object storage. You must allocate storage size to this Zabbix server in Gibibyte. The allocated storage size will be deducted from your company quota. You can only allocate as much size as your company has left on its quota.
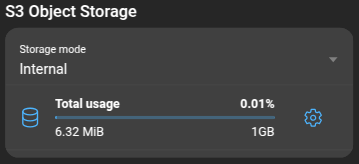
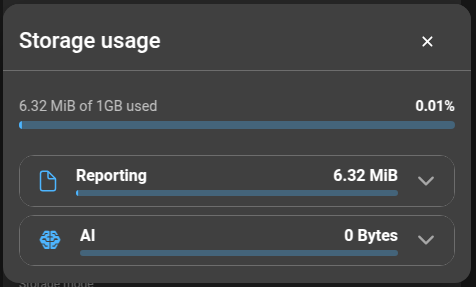
When clicking on the Total usage, it will open a dialog with a breakdown of the space usage:
External
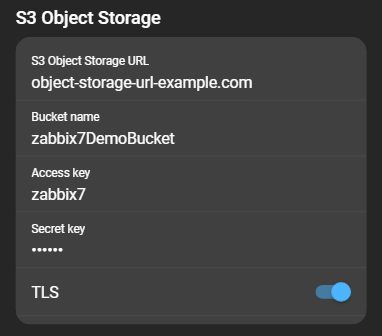
You can also use your own S3 object storage by selecting External. When choosing external, you must provide the following information:
- Object storage URL: The URL of the object storage that should be used.
- Bucket name: The name of the bucket the deliveries will be stored in.
- Access key: The access key name to use for authentication with the storage provider.
- Secret key: The secret key to use for authentication with the storage provider.
- Require TLS: A toggle to configure if TLS is required or not.
If using an external S3 server, make sure that you use an individual S3 bucket per Zabbix server.
Disabled
When S3 object storage is disabled, no S3 storage will be configured for this Zabbix server and DataForge Reporting and AI will be disabled.
When switching the S3 object storage mode from Internal to something else, it will delete your internal S3 bucket and all its content, including reports, AI datasets, AI models, and AI tests.
The S3 housekeeper ensures that the storage is not filled with data that is no longer required. If data created in DataForge, such as an AI model, is deleted in DataForge, it is also deleted from S3 storage.
3. AI runners
You can register and manage your AI runners in this section. These are necessary for our AI feature in DataForge.
Click Register a new AI runner to open a form:
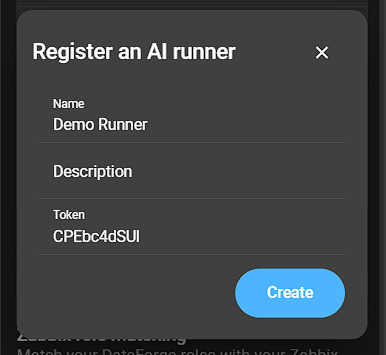
- Name: Provide a name to your AI runner.
- Description: Provide a description to your AI runner.
- Token: This token is user to register your runner. Has to be provided in your AI runner configuration file.
Click Create to register your AI runner. It will now show in the list:
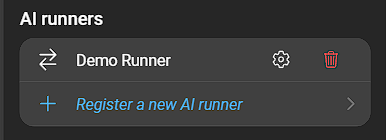
- To change it’s configuration click the Cog wheel icon.
- To remove the AI runner click the Bin icon.
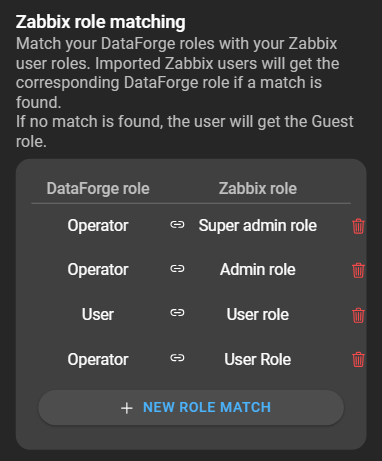
4. Zabbix role matching
Zabbix role matching allows the manager to specify how the user roles will be assigned when importing Zabbix users. More details about this feature can be found in chapter Role matching.
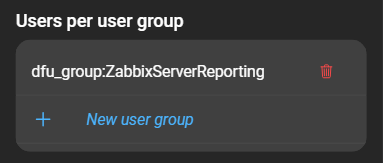
5. Users per user group
Shows which user groups are established on the server. You can create and manage user groups, which are necessary when working with DataForge’s Reporting feature, explained further in chapter DataForge user groups.
6. User configuration
You can access Imported Zabbix users to import users from Zabbix, manage imported users or impersonate them.
More details about importing and managing users can be found in chapter Import Zabbix users.
More information about impersonating is found in chapter Impersonating.
Synchronize now
You can manually synchronize DataForge and the Zabbix server by opening the context menu of a server and clicking synchronize now. This ensures that DataForge works with the up-to-date data of the Zabbix server.
This is usually not necessary as DataForge synchronizes regularly by itself.
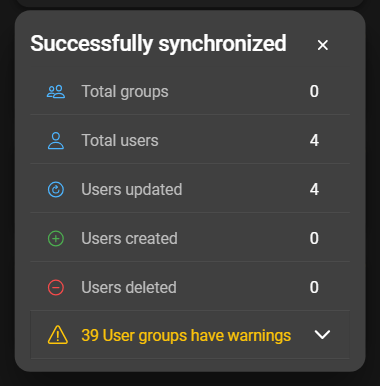
When the synchronization has been completed, the results show the number of updated entities. In addition, warnings or errors are displayed. The warnings and errors section can be expanded, but is also accessible in the server details.
Verify the connection and credentials
To verify the connection, open the context menu and select Analyze Connection. The results of the connection test will then be displayed.
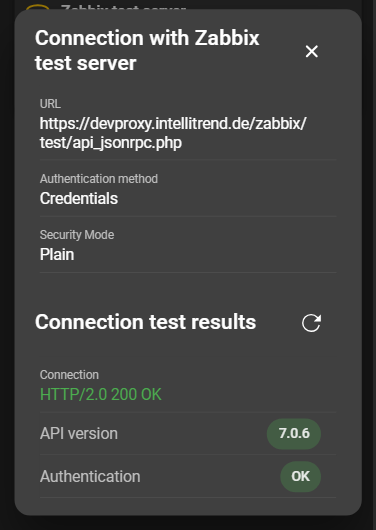
There are four different outcomes the connection test can have:
- The Connection chip is red and displays
ERROR, indicating that no connection can be established. This is most likely due to an issue with the URL. - The API version chip is red and displays
ERROR, suggesting that a connection can be established, but the endpoint is not a Zabbix API. - The Authentication chip is red and displays
ERROR, indicating that the Zabbix API can be reached, but the credentials of the root user are incorrect. - Everything is okay when the Connection, API version, and Authentication chips are displayed in green, as shown in the image above, indicating that the connection and authentication are successful.